In the
last post, we went through building the root CA which followed building the domain and generating a mess of test users. Moving along this time, we're going to start building the issuing CA for the domain and for our network devices. Once we get through this stage, the root CA can be powered down, and moved to long term permanent storage if necessary.
Once again, I'll be using the
The 70-640 Self-Paced Training Kit from Microsoft Press as my guide, though the
MCTS 70-640 Cert Guide from Pearson will work as well. I actually prefer the Pearson book as it feels more in depth and complete than the Microsoft Press book.
First, ensure that the root CA and issuing CA are both running. Log into the issuing CA with an administrator account. As with the root CA, you can use a local administrator on the issuing CA, but a domain administrator will be fine as well. And unlike the root CA, if you are using Server 2008 or 2008R2 for the issuing CA, it needs to be Enterprise or Data Center Edition. For Server 2012 and up, Standard Edition will be sufficient.
I'm really liking the decision now to go with Server 2008R2 for the root CA ,Server 2012R2 for the issuing CA, and Server 2016 for the domain controller. The contrasting appearances of windows in the three operating systems really helps to make it clear which server is which in the screen shots.
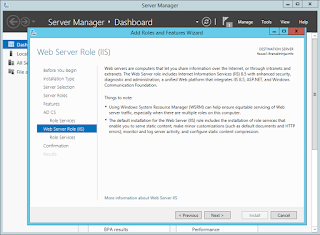
Enough of the small talk, let's get started. Launch Server Manager if it is not already running. As with setting up the domain controller, start by selecting add roles and features.
Select the local server from the list if it is not the only one, just proceed if it is.
Select Certificate Authority from the list, and accept the prerequisite roles and features to be added.
There won't be any additional features to add, so just Next your way through.
Now options for the CA role appear.
Here we'll select Certificate Authority and Online Responder. We'll be adding NDES later. With 2008 and 2008R2, you couldn't install NDES at the same time as any other CA role. I don't recall if that is true still for 2012R2, but I'll just go with what I know here.
We'll have the options to configure IIS next.
The necessary IIS bits will be preselected, add any thing else you may want.
We're now at the confirmation screen where you get one last chance to go back. Hit install whenever you're ready.
Everything selected will install.
Once the installation is complete, you'll find yourself back at Server Manager. If you click on AD CS on the left, you'll notice that additional configuration for the AD CS role is required. On the yellow bar, first click More, then configure.
Here is a dialog box giving you information about what needs to be done. Click Configure again.
First, you will need to provide credentials. Give the currently logged in user, or provide a username/password for a different user.
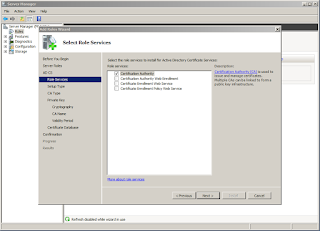
Select both Certification Authority and Online Responder to configure.
Select Enterprise CA. If you don't have the right edition of Windows Server, this option will be grayed out.
Next, select subordinate CA.
Create a new key.
Select your cryptography options. I went with all the same options as before. You can lower the strength if resources are at a premium.
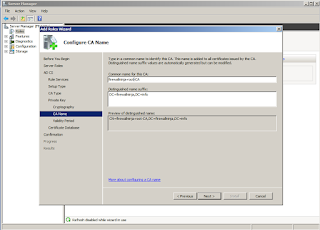
Here we'll name the CA. Again, this is not the same as the server's hostname. The defaults are fine.
Here we'll specify that we want to get a certificate from our root CA. Click the radio button next to Send a certificate request to a parent CA, and then hit the Select button and choose the root CA.
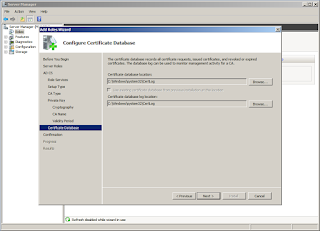
Here's where the data files will live for the CA. The defaults are fine for a lab server.
Confirmation of your settings.
Finish up the wizard and allow the configuration to take place.
Now, create a file share somewhere on the issue CA. You'll be copying your cert to this share from the root CA later. If you need a refresh on creating a share,
Technet has you covered.
Finally when it is done configuring, you're ready to bring the issuing CA online. Go back to the root CA and load the Certification Authority mmc. In the Pending Requests folder, you'll see the request from the issuing CA. Right click on this request and select issue.
Now you'll see that the cert has moved from Pending Requests to Issued Certificates.
Right click on it again and export the cert. Once you have it on the HDD, move it to the file share on the issuing CA. For some reason on mine, it saved with a long random name with .tmp as the extension, but it worked.
Back at the issuing CA, right click on the server name and select All tasks, Import. If you got a .tmp file as well, you'll have to change file type to All Files in the open dialog box.
You'll notice that there really isn't much difference in the layout and functionality of the CA mmc on the two different operating systems. When you really dig in, there will be additional features in 2012R2, but other than that it's minimal and cosmetic.
With the certificate installed, you'll finally be able to start up the Certification Authority service. From the CA mmc, right click on the server and select All tasks, start service.
Now that your issuing CA is up and running, wait through another group policy update cycle (roughly 90 minutes) and then you can shut down your root CA.
Note that the issuing CA will not appear in the Certification Authorities container in Active directory as the root CA did. Instead, check the Enrollment Services Container, which contains all CAs for Active Directory, not just the root CA. For the purpose of this post, verification of the issuing CA is enough, but if you care to know more about the matter, you can find some great information
on Technet. I'll certainly cover more in depth information like this as my work in the lab gets to it.
The last step here is to install and configure the NDES service on the issuing CA, but this post is long enough so I'll save that for another post.