After tiring of the trips up and down the stairs dealing with a physical 3750 switch and Windows 7 workstation testing 802.1x, I decided to give it a shot virtually. And I'm pleased to report that it works like a champ. This post is not a how to guide on setting up 802.1x, it's to show another complex configuration topic that can be done exclusively in the virtual domain. And while I've never done it personally, I've seen elsewhere that it's also possible to do in EVE-ng.
I setup a basic topology in GNS3. In the light blue oval is the connection to the physical network. The cloud connects to VLAN10 on my physical 3750 switch, which is the home network. There's a generic GNS3 switch there just in case I want to tie anything in at that point in the future, but at this point it's unnecessary and not really being utilized. Next we have BB2, which is a IOU router (i86bi-linux-l3-adventerprisek9-15.4.1T.bin if you care) that provides a degree of separation between the "real network" and the test area. SW11 is a L2 IOU image (i86bi-linux-l2-adventerprisek9-15.2d.bin) playing the role of the supplicant in the chain. And finally we have fn-ws70008, which is a domain connected Windows 7 workstation which runs in qemu on the GNS3 VM. The Yellow section branches out into another area of the topology that isn't relevant to this discussion.
Be advised that using a nested VM like this (qemu VM running inside of the GNS3 VM) is horrible from a performance standpoint. However the performance is not bad enough that delays lead to timeouts, so I can live with it for now.
At this time, I'm using the Windows 7 VM to confirm both 802.1x and MAB operation. I had a basic VPCS host that I tried to use for MAB, but for whatever reason, the switch didn't want to play nice with that host so I just set it to try both but prefer 802.1x on the Windows 7 workstation so I could see both play out in the ISE logs. If you can get a MAB authentication to trigger with a VPCS host or a router, I'd love to hear about it.
Turning our attention over to ISE, the next 2 images show the basic NAD configuration for SW11. Nothing out of the ordinary here, straight out of the documentation.
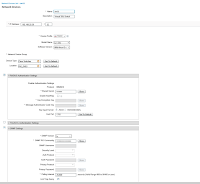
The switch configuration comes straight from the SISAS certification guide in Chapter 12. You can also find a great stand alone PDF right here from Cisco. As far as I recall, everything in the cert guide and the PDF work in this version of the L2 IOU imageexcept for LLDP device tracking (Edit: its working now with no changes on my part. No idea why it didn't before). CDP and DHCP tracking work, so that's definitely not the end of the world. One caveat to keep in mind is that ip routing is enable by default on these switches which led to a short session of head scratching when I couldn't reach anything off of the local network from the switch the first time I started seriously labbing with it.
From what I can tell, the L2 IOUv works great as well, however I haven't labbed to seriously with it yet since the L2 IOU image does everything I've asked of it and I've been using it since before IOUv was a thing. As another note, there is a significant syntax difference with IOU 15.6 so I'm holding off on that one as well.
Configuring ISE for 802.1x is also straight from the SISAS certification guide, so no need to beat a dead horse rehashing it here. Chapters 10 and 11 cover AuthZ and AuthC policy creation. So with all that completed, let's check the Live Log in ISE. For the record, I'm running ISE 2.0 with no patches applied.
Here we'll see the workstation performing MAB and 802.1x authentication successfully. You'll also note the switch doing the automate-tester authentication with the local-bob account. For ease of use, I have an AD account called domain-bob, a local account on ISE called local-bob, and each router has a username called router-bob. Thanks to Keith Barker inspiring me to name all the users Bob, though I at least saw the potential for confusion with both the domain user and ISE user being just "bob."
And as one last show of compatibility, I've configured sw11 to send syslog to my local Splunk server. I do use the ISE interface for debugging as much as possible while labbing, as you should when you're trying to learn everything about ISE, having one location for long term log retention for troubleshooting purposes is very valuable when the problem involves multiple devices, and/or you want to look back at the messages for a similar situation that did work.
Be advised that using a nested VM like this (qemu VM running inside of the GNS3 VM) is horrible from a performance standpoint. However the performance is not bad enough that delays lead to timeouts, so I can live with it for now.
At this time, I'm using the Windows 7 VM to confirm both 802.1x and MAB operation. I had a basic VPCS host that I tried to use for MAB, but for whatever reason, the switch didn't want to play nice with that host so I just set it to try both but prefer 802.1x on the Windows 7 workstation so I could see both play out in the ISE logs. If you can get a MAB authentication to trigger with a VPCS host or a router, I'd love to hear about it.
Turning our attention over to ISE, the next 2 images show the basic NAD configuration for SW11. Nothing out of the ordinary here, straight out of the documentation.
The switch configuration comes straight from the SISAS certification guide in Chapter 12. You can also find a great stand alone PDF right here from Cisco. As far as I recall, everything in the cert guide and the PDF work in this version of the L2 IOU image
From what I can tell, the L2 IOUv works great as well, however I haven't labbed to seriously with it yet since the L2 IOU image does everything I've asked of it and I've been using it since before IOUv was a thing. As another note, there is a significant syntax difference with IOU 15.6 so I'm holding off on that one as well.
Configuring ISE for 802.1x is also straight from the SISAS certification guide, so no need to beat a dead horse rehashing it here. Chapters 10 and 11 cover AuthZ and AuthC policy creation. So with all that completed, let's check the Live Log in ISE. For the record, I'm running ISE 2.0 with no patches applied.
Here we'll see the workstation performing MAB and 802.1x authentication successfully. You'll also note the switch doing the automate-tester authentication with the local-bob account. For ease of use, I have an AD account called domain-bob, a local account on ISE called local-bob, and each router has a username called router-bob. Thanks to Keith Barker inspiring me to name all the users Bob, though I at least saw the potential for confusion with both the domain user and ISE user being just "bob."
And as one last show of compatibility, I've configured sw11 to send syslog to my local Splunk server. I do use the ISE interface for debugging as much as possible while labbing, as you should when you're trying to learn everything about ISE, having one location for long term log retention for troubleshooting purposes is very valuable when the problem involves multiple devices, and/or you want to look back at the messages for a similar situation that did work.
BB2 is also configured with ip-helper to forward DNS requests to one of my Windows domain controllers, both of which exist outside of this GNS3 topology. That also works flawlessly.
So bottom line is that I'm really liking these IOU images (both L2 and L3) and they're almost fully meeting my labbing needs. Since more recent ISE versions appear to work in GNS3 as well, you could theoretically work through the SISAS almost completely in GNS3 at this point. Connecting the dots in the exam topics tell me I still want to know ACS, though I cannot say for sure. It's not specifically listed on the topics and I haven't taken the exam yet. But the exam is written for ISE 1.2 (which doesn't have TACACS+ support) and the topics do say implement device administration with both TACACS+ and RADIUS.
Next up, 802.1s on NX-OS using the Cisco Nexus 1000V switch image, though I'm not sure when I'll get around to that. Nexus switches do not appear anywhere in the security track (yet) but I do want some exposure to them. Maybe I can integrate a 1000V image into ESXi and ditch the nested Windows 7 VM.








